Thoughts on Google Apps Two-Step Verification
Between my posts about SSH tunnels, VPNs and whole disk encryption, you might gather that I am a bit more paranoid about computer security than the typical web user. It started in 2006 during my Yahoo! internship when I used an RSA SecurID token — my first brush with two-factor authentication. A few weeks ago Google released a small feature that made my ears perk up: two-step verification. It is currently only available for certain Google Apps account types: Premier, Education, or Government Edition. Previously, the security conscious could only get two-factor authentication with their Google Apps account with a custom software setup: Google Apps SSO with WiKID Server and a Gheimdall plugin. The new Google Apps Two-Step Verification addition makes that custom setup a thing of the past.
Why?
Why does two-step verification make me ecstatic? You've no doubt read those security nightmare stories over the years. Some malevolent-minded person gets access to a victim's Gmail account then searches for things like GoDaddy email confirmations, past transactions, passwords and so on. They can even setup email forwarding to their email address so the victim would never know security had been breached1 . In less than 24 hours, the attacker can have gained access to dozens of other accounts owned by the victim, changed domain name ownership and more. Many peoples' entire online lives center around their precious Gmail account.While this new feature is largely aimed at businesses looking to migrate corporate email and tools to the Google Apps suite while maintaining the familiar and secure two-factor auth configuration, it is definitely welcomed by power users as well. In fact, it will be offered on all Gmail accounts within the next few months (according to TechCrunch).
Related: Google just released a handy Gmail security checklist.
What?
Two-factor authentication adds one more barrier to entry for people looking to gain access to your Google Apps account. After the regular password login, the user is prompted for a second "password." This is not a user-set password, but rather a generated and time-sensitive code from a token device (in this case, your mobile phone).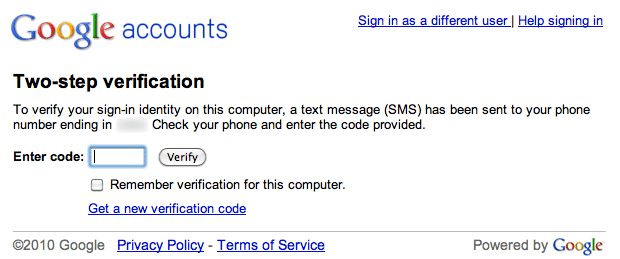
Google Apps Two-Step Verification - This is displayed after providing your regular password.
Two-factor authentication typically is a signing-on process where a person proves his or her identity with two of the three methods: "something you know" (e.g., password or PIN), "something you have" (e.g., smartcard or token), or "something you are" (e.g., fingerprint or iris scan).
Everything you ever wanted to know about two-factor authentication can be found at Wikipedia.
Setup
Since Two-Step Verification is a new feature for Google Apps rather than only Google Apps Gmail, it must be enabled in the actual Google Apps admin panel. Login at https://www.google.com/a/yourdomain.com, or simply click Manage this domain within Gmail. Once you are in the Google Apps admin panel, browse to the Advanced tools tab and scroll down to the Authentication section. Click the Allow users to turn on two-factor authentication checkbox.
Enable two-step verification in Google Apps
Two-step verification is now available for users under that Google Apps domain to setup themselves in their Gmail. Visit your Google Apps Gmail account settings and go to the Accounts tab. Click the Google Account settings link at the bottom.
On the next page, click Change sign-in verification and open it in a new browser tab.
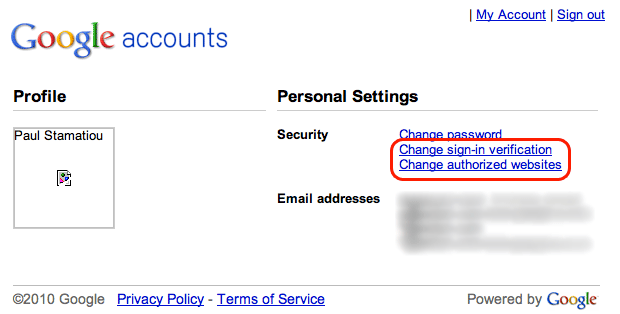
Google Account Security Settings
Then select the radio button for "Two-step verification, by password and verification code (sent via SMS, phone call, or mobile application)."
Sections will appear for configuring your mobile application, phone as well as something called single-use codes. If you have an Android device, iPhone or BlackBerry smartphone, you will probably opt for configuring the Google Authenticator mobile application. Alternatively, you may wish to have Google call or send a text message so that you don't have to find and launch the Google Authenticator app amongst your billion other mobile apps.
Google Authenticator is a mobile application that allows you to generate two-step verification codes on your smartphone without a network connection. We recommend users with smartphones to use Google Authenticator to generate verification codes instantly to sign in to their Google Apps accounts.
I configured both but only the last one I configured (the mobile app) remained active, despite the Sign-in verification page showing both methods as properly configured and not hinting as to which one takes priority. I would suggest setting up the mobile app if you can. You might find yourself in a foreign country at an Internet cafe where your phone does not have service and you need to pass two-step verification to access your Google Apps Gmail.
Then again, you can always use a lifeline in a rare case like that. Err, I mean single-use code. Google provides all two-step verification enabled users with a set of codes that may be used as your verification code just once. Keep these numbers within reach for emergencies but don't keep them too handy. The truly paranoid won't keep these single-use codes in a digital format — perhaps printed off and stored in a bank safe deposit box. Or elsewhere if they don't trust the government2 . Actually, the truly paranoid don't use Google Apps, but I digress.
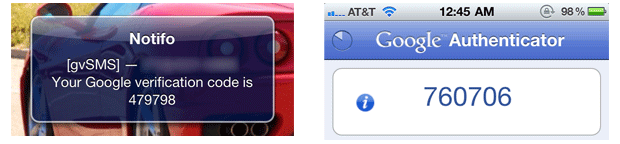
Two (of three) ways to receive verification code for Google Apps Two-Step Verification: via SMS and generating a code with the Google Authenticator mobile app
What are Access Codes?
How do you give access to your Google Apps account for desktop and mobile applications that don't have a field for the verification code? In place of your regular password, you provide that application with an access code. It's like a one-off password for just that application. Get started by clicking Change authorized websites from the account settings page you originally loaded from Gmail settings.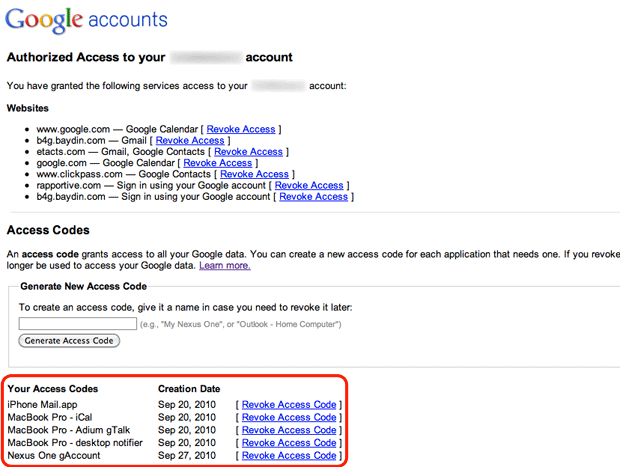
Google lists websites you have authorized to have access to your account, as well as letting you manage access codes for each service/application.
Simply create a new access code by providing a descriptive title so you can keep track of it later. Then copy that code and supply it to the application or service for which you made it. An example might be your desktop mail client that accesses Google Apps Gmail via IMAP. The downside is that you will have to let your computer save this access code (or remember a very long and entropic code). It's not something you can just type in only when you feel like accessing that service, like logging into Google Talk and typing in your password each time.

Creating a new access code
The upside is that you can easily revoke access to your account for that application if that particular computer or device becomes compromised — without all the hassle associated with having to change your password and subsequently update it on all your Internet-connected devices.

Easily revoke any access code.
Thoughts
I think I have sufficiently covered the basics of what Google's new two-step verification feature is about, why you might want to consider enabling it and everything else you need to know to get it all setup. If you have any questions, please let me know in a comment below. Two-step verification for certain Google Apps accounts (and surely more in the near future) is a welcomed addition. It is not the world's most bulletproof solution 3 but it is definitely much better than a regular password-protected account. Even better if you use it in conjunction with a crazy password4 .But won't this be annoying to do every time I need to check my Gmail? On your personal computer you will likely check the "Remember verification for this computer" checkbox when logging in, which gives you 30 days of access without having to provide the verification code again (barring any browser resets)3 .
I give Google Apps Two-Step Verification 9 out of 10 Stammys. It would be higher if other tokens were allowed. Relying strictly on a mobile device is great because everyone already has one but they can too easily be lost, stolen or bricked (botched iPhone jail-breaking anyone?). There's a good chance that if someone's laptop bag is stolen, their mobile phone will be right there with it. Keychain-based tokens, not so much. Adding support for USB tokens or SecurID/CryptoCard tokens would be the next natural step, especially as Google Apps is primarily targeted towards the enterprise. Just my 2 cents.
Thoughts? Will you enable two-step verification when your Google Apps or Gmail account gets it?
1 It doesn't help that Google's whole marketing pitch with Gmail is that you'll never have to delete email again because of all the storage space.
2 Authorities in the U.S. can access safe deposit boxes with probable cause. Then again, if they really wanted to get access to your Google Apps Gmail account they could just poke Google, who would hand them the info they needed on a silver platter thanks to the 1986 Stored Communications Act. IANAL
3 30-day browser cookie set by users that click the "Remember verification for this computer" checkbox means that if your computer is stolen, the thief can still access your account without having to provide the second step of verification, and likely not even the password if your computer was just sleeping and browser already open. However, this is a small risk on the grand scheme of things for the security paranoid that have their computer prompt for a password on wake, run services like Prey, and even have disk encryption.
4 Have you tried 1Password's strong password generator? It makes passwords like efihGiT{NZiAU+dCz4^yx4Y8d}ZG8C}eG=fGmBx^6pDnhbaRHm

